Wi-Fi security protocol WPA2 (Wi-Fi Protected Access 2) is vulnerable to Key re-installation attacks as per Security researcher Mathy Vanhoef who has made a public announcement regarding this WPA2 vulnerability. This serious exploit in the WPA2 standard protocol has been code named KRACK which uses the key re-installation technique that allows attackers to eavesdrop on the information exchanged between the wireless access points and clients.
A flaw in WPA2’s 4-way handshake authentication process can be exploited by hackers to steal data which would be encrypted otherwise, based on the research carried out by Mathy Vanhoef of KU Leuven in Belgium. Hence, all the wireless devices which use WPA2 for authentication is likely affected by this vulnerability. The Computer Emergency Response Team (CERT) of the US government has issued a security bulletin about the flaw to warn all the vendors for providing patches to fix this issue.

WPA2 remains the Wi-Fi standard for authentication and encryption across all vendors since its introduction in 2004. Previously WPA1 and WEP (Wired Equivalent Privacy) protocols were used but they also have multiple security weaknesses which led to introduction of WPA2. The KRACK attack involves exploiting the key management vulnerabilities in the 4-way handshake process of WPA2 security protocol. The attacker can manipulate the handshake process to induce nonce and session key reuse which will result in key reinstallation by the Wireless client or Access Point (AP). An attacker who lies within the wireless range of the affected AP and client can use this vulnerability for different type of security attacks such as HTTP content injection, Ransomware code injection, TCP connection hijacking, packet replay attacks and also arbitrary packet decryption and injection.
The CERT and the security researcher Mathy Vanhoef from KU Leuven University have publicly disclosed these vulnerabilities on 16th Oct 2017. The research paper titled “Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2 “by Mathy Vanhoef explains all the techniques which are used for performing these attacks. He has also released a demonstration video on how this KRACK attack can be used to intercept data from an Android phone using some sophisticated scripts to force nonce and session keys re-installation.
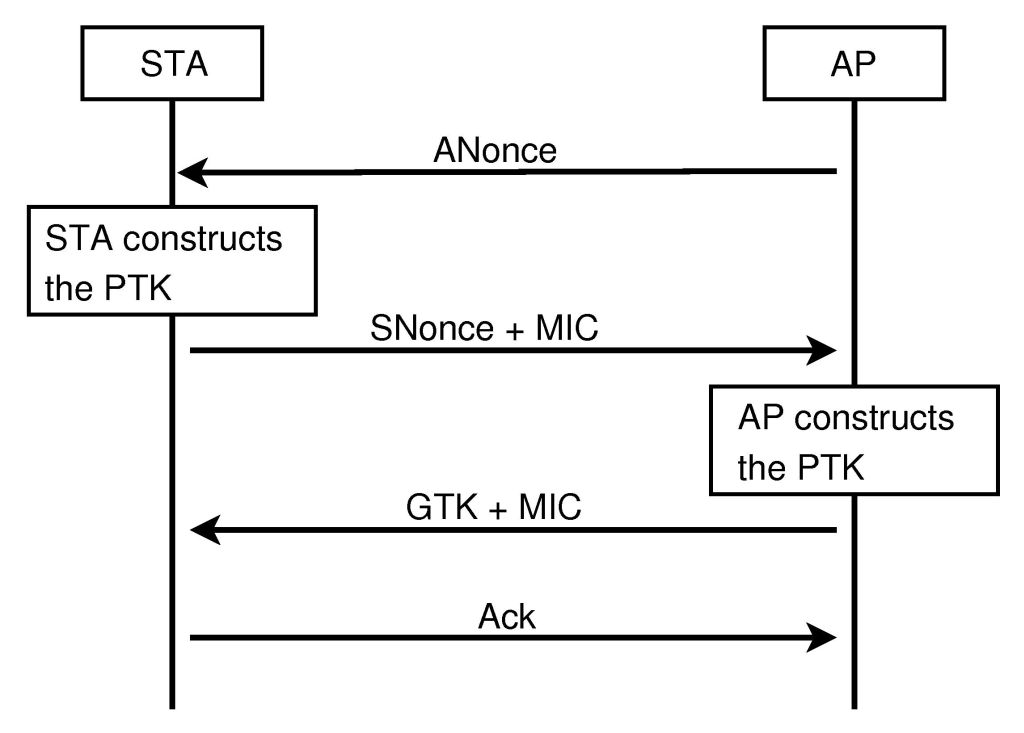
The KRACK attacks are targeted towards all the Wi-Fi compatible clients that use WPA2 protocol. The operating systems which are majorly affected include Android and Linux. It has been identified based on the research that 41% of all Android devices running with Version 6.0 and above are especially vulnerable to this WPA2 exploit. The other operating systems include macOS, Windows, openBSD and iOS.
Microsoft has already released a patch to fix this vulnerability on October 10 and have announced that all the Windows users who have installed this latest Security Update will be automatically protected from the vulnerability. Even Apple has already patched the vulnerability in the developer betas which are available currently for their macOS, watchOS and iOS. They also plan to make the fixes available in the public betas very soon. As for Android, Google spokesperson mentioned that they are aware of the issue and working on the fix. They will initially provide the fix through the Security update that will be released on Nov 6th for their Pixel phones. Further security updates with fixes for all Android platforms will be released for all devices in upcoming weeks.
How to Secure Yourself?
Since all the wireless devices are affected by this vulnerability, most of the users will start to panic on knowing about this exploit. But there are some things you should understand about vulnerability first. An attacker cannot obtain your Wi-Fi password using this vulnerability and can’t launch any remote attacks. He should be within your wireless range in order to use this exploit. He can only intercept traffic between your device and Wireless Access point. If your data is encrypted properly using HTTPS (Hyper Text Transfer Protocol Secure), then he won’t be able to intercept this traffic. There are some important tips which you can follow to safeguard yourself from any malicious attacks due to this WPA2 vulnerability.
- Update all your wireless devices including tablets, phones, Wireless routers, Access points etc. with the latest security patches. If you are a Windows user, you already have security update available from Microsoft which you can install. Similarly, many other Wireless product vendors have already provided fixes which is available online. Enable auto-updates on your devices to ensure that they have the latest security patches installed automatically.
- Use Ethernet temporality if your Wireless Access points or routers do not have the security patches available yet. You can turn off Wi-Fi in all your home devices and use Ethernet wired connection instead. This will ensure that you don’t get exposed any WPA2 vulnerability attacks.
- Always use HTTPS when browsing to ensure all your data is encrypted. You can make use of HTTPS Everywhere extension which is available for all browsers like Chrome, FireFox and Opera. By using this extension, you can ensure that all the web traffic is encrypted using SSL protocol (Secure Sockets Layer) and this will make it difficult for any hacker to intercept the traffic.
- Use Mobile data on your phones instead of Wi-Fi till you get the security patches available for your device. You should definitely avoid using public Wi-Fi in airports or coffee shops as you will be prone to eavesdropping and other man-in-the-middle attacks. You can pay extra for mobile data and use it till the WPA2 vulnerability fixes are available for your phone. You should definiltey consider this option if you are using an Android device running with version 6.0 and above.
- You can also use a secure VPN solution to ensure that all your data is encrypted and cannot be intercepted by the attacker.
- If you have a lot of IoT devices in your home like Wireless security cameras, smart speakers and other gadgets, try to find out if there are security patches available for all these devices. If they are not available, ensure to remove the risky devices from your wireless network until the fix is installed.
Vanhoef will be presenting his research on Nov 1 at the Computer and Communications Security (CCS) conference. As a Wi-Fi user, you should aware of the latest updates happening around this vulnerability and keep your devices updated whenever the fixes are available. Meanwhile, the members of Wi-Fi alliance have asked the users not to panic as there is no known attacks which has made use of this vulnerability. They also mentioned that they will be conducting tests for this vulnerability within their global certification lab network. They have also provided a vulnerability detection tool for the existing Wi-Fi alliance members to check if their devices are affected.

